Privacy Impact Assessment
Overview
It is a system for preliminary investigation, analysis and assessment to analyze and improve the risk factors before adopting anew or changing personal information files
Legal Ground and Objects
- (Legal ground)Article 33(privacy impact assessment) of the Personal Information Protection Act
- (Object institutions)Public institutions that will establish or operate personal information files prescribled in Article 35 of the Enforcement Decree of the Act, or change or connect the existing system
Objects of mandatory privacy impact assessment
When establishing or operating personal information files
When changing personal information files
- - In the case of establishing, operating or changing personal information files of at least 1 million data subjects
- - In the case of establishing, operating or changing personal information files of at least 500,000 data subjects upon connecting internal and external system
- - In the case of establishing, operating or changing personal information files of at least 500,000 data subjects if the data contains sensitive information, such as medical information, or personally identifiable information, such as resident registration number, etc.
When changing personal information files
- - In the case of changing the operating system of personal information files, such as personal information searching system, after the privacy impact assessment
Procedure
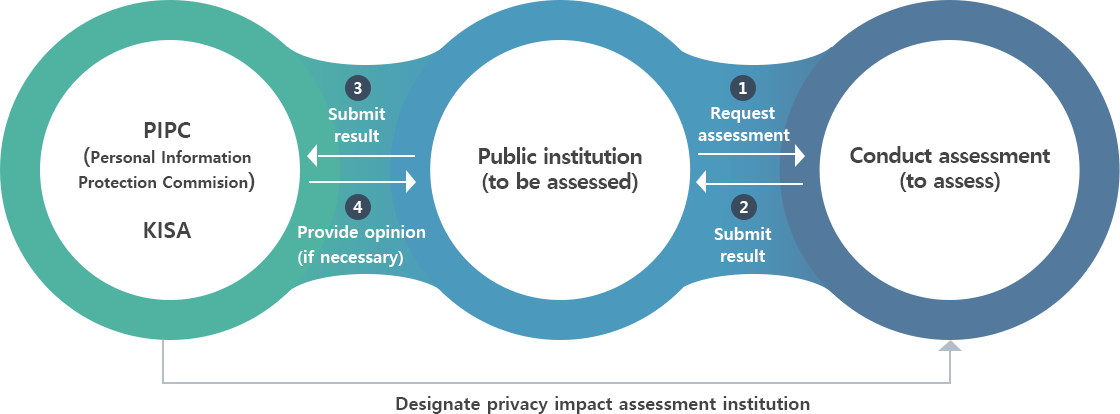

- Personal Information Protection Commission KISA
- Public Institution (Object institutions)
- Conducting assessment (Privacy impact assessment institution)
- Requesting assessment
- Submitting the result
- Providing opinions (if necessary)
- Designating the privacy impact assessment institution
Assessment Procedures
- (When is the assessment conducted) The assessment is conducted in the stage of analyzing or designing the personal information processing system before establishing the system
- (Who conducts the assessment)The assessment is conducted by privacy impact assessment team which is comprised of the person in charge in the department of the assessment, the privacy officer, the person in charge of personal information protection, etc.
* Public institutions request the assessment to the privacy impact institution designated by the Personal Information Protection Commission
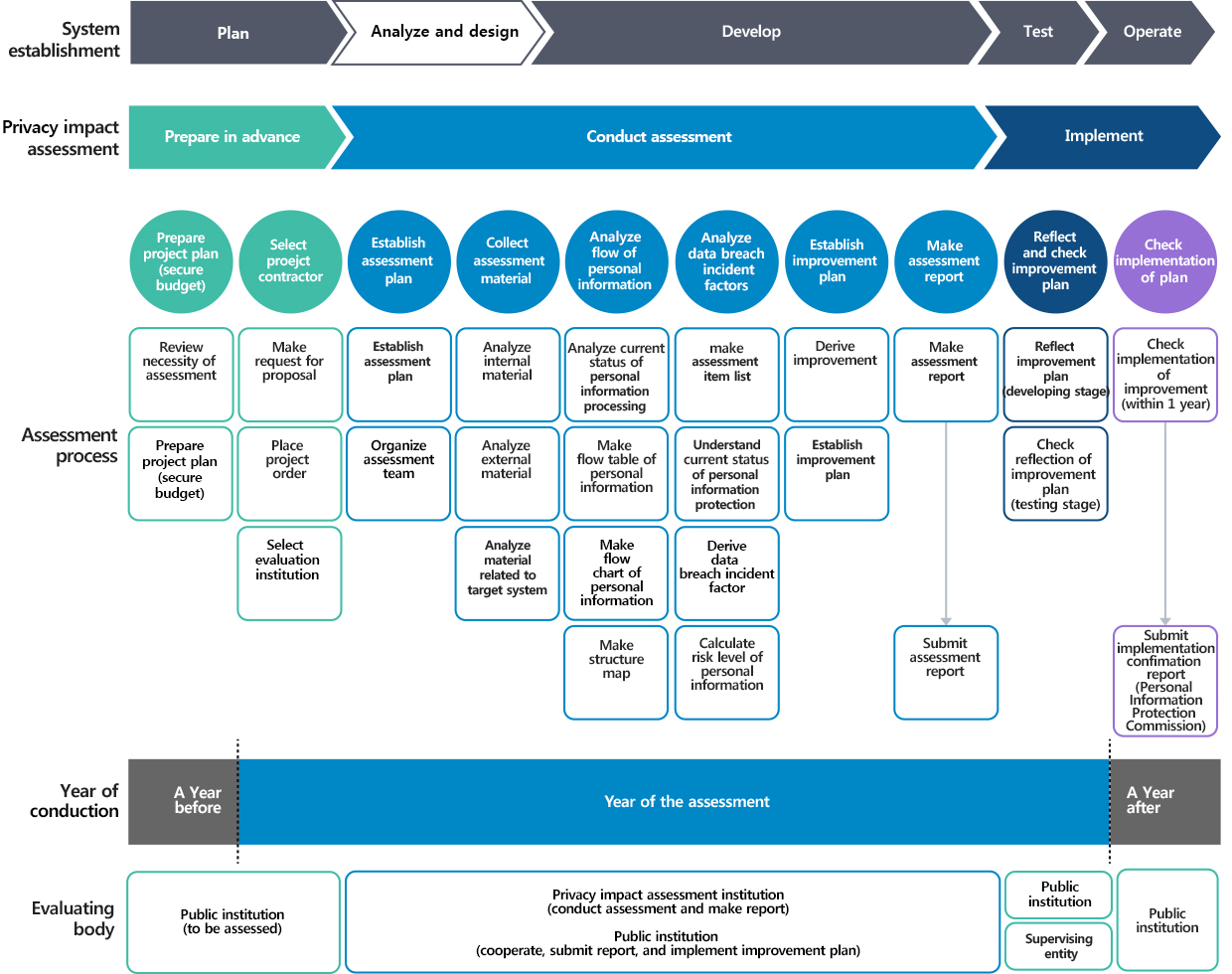
 Enlarge image
Enlarge image
- Privacy impact assessment
- Preparing in advance
- Conducting the assessment
- Implementing
- Preparing project plan (Securing budget)
- Selecting proejct contractor
- Establishing assessment carry-out plan
- Collecting assessment materials
- Analyzing the flow of personal information
- Analyzing infringing factors
- Establishing improvement plan
- Preparing assessment report
- Reflecting and checking improvement plan
- Checking implementation status
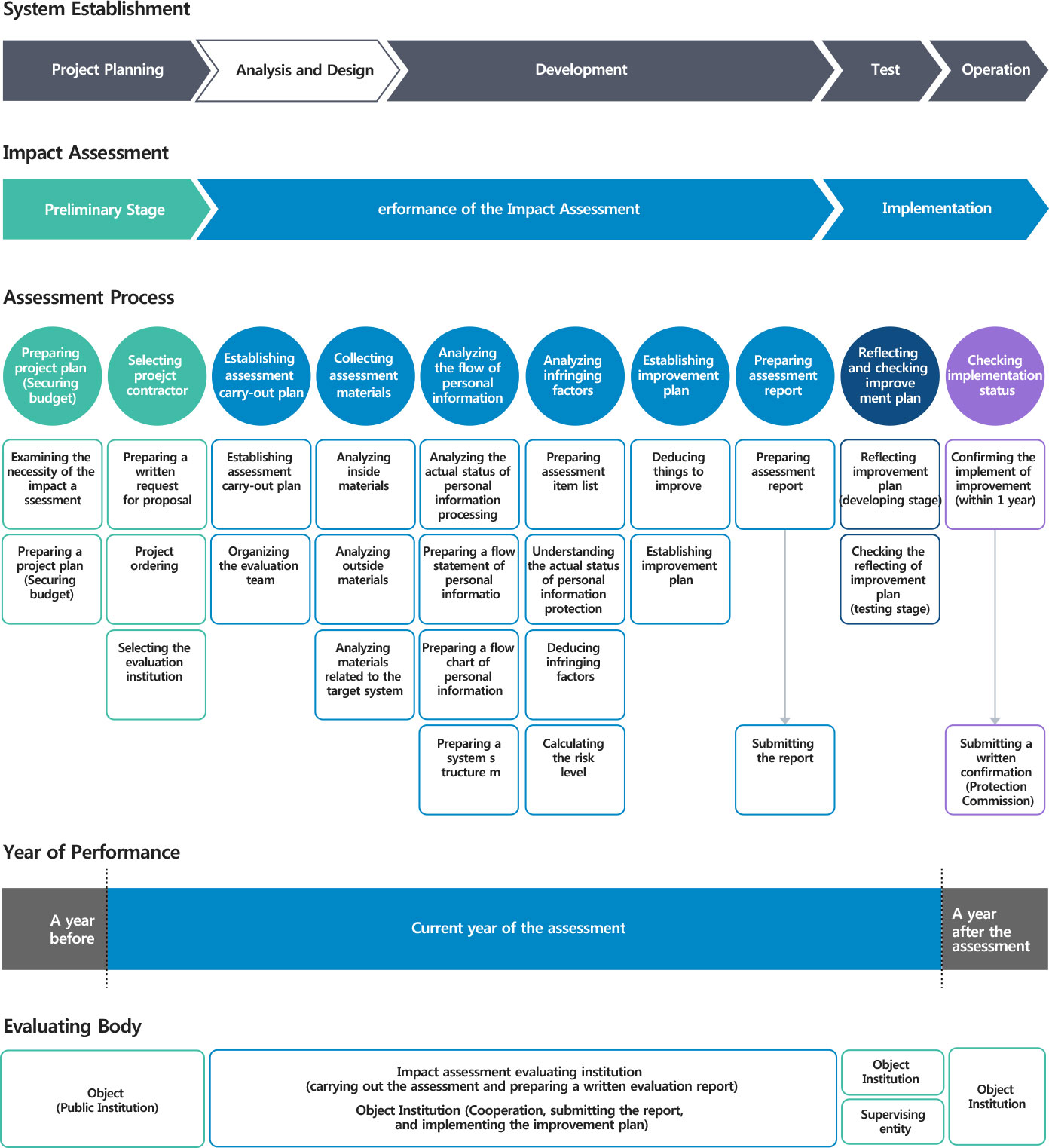
- Assessment Process
- Examining the necessity of the impact assessment
- Preparing a project plan (Securing budget)
- Preparing a written request for proposal
- Project ordering
- Selecting the evaluation institution
- Establishing assessment carry-out plan
- Organizing the evaluation team
- Analyzing inside materials
- Analyzing outside materials
- Analyzing materials related to the target system
- Analyzing the actual status of personal information processing
- Preparing a flow statement of personal information
- Preparing a flow chart of personal information
- Preparing a system structure map
- Preparing a system structure map
- Preparing assessment item list
- Understanding the actual status of personal information protection
- Deducing infringing factors
- Calculating the risk level
- Deducing things to improve
- Establishing improvement plan
- Preparing assessment report
- Submitting the report
- Reflecting improvement plan (developing stage)
- Checking the reflecting of improvement plan (testing stage)
- Confirming the implement of improvement (within 1 year)
- Submitting a written confirmation (Protection Commission)
- Year of Performance
- A year immediately before
- Current year of the assessment
- A year immediately after the assessment
- Evaluating Body
- Object (Public Institution)
- Impact assessment evaluating institution (carrying out the assessment and preparing a written evaluation report)
- Object Institution (Cooperation, submitting the report, and implementing the improvement plan)
- Object Institution
- Supervising entity
- Object Institution
Expected Effects
Minimizing the risk of privacy infringement at the stag of establishing and operating the system to prepare effective responses by reviewing and improving the risks from the stage of designing the system.